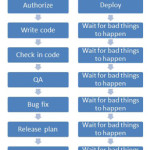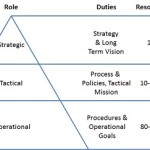
When discussing organizational management, a critical aspect is the balance between Strategic, Tactical, and Operational roles and duties. Have you ever seen companies where the employees complained that: The directors and upper level managers keep sticking their nose in the day-to-day operations and making a mess of things. Major processes keep getting re-defined and no …
Read more